But when i put internet interface into separate vrf ipsec fails.
Cisco ipsec front door vrf.
I d like to configure dmvpn hub behind static nat.
The routing instance that is used if no specific vrf is defined.
Idea here is to have underlay network running in a vrf often called fvrf or front door vrf.
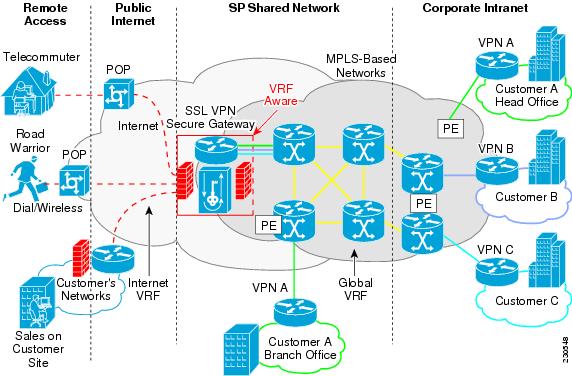
Vrf aware ipsec functional overview front door vrf fvrf and inside vrf ivrf are central to understanding the feature.
While this provides a substantial level of isolation it does nothing to hide the contents from prying eyes in untrusted parts of the transit network.
When internet interface and tunnel interface are in the same vrf on the hub everything works well.
The outer encapsulated packet belongs to one vrf domain called the front door vrf fvrf while the inner protected ip packet belongs to another domain called the inside vrf ivrf.
Stated another way the local endpoint of the ipsec tunnel belongs to the fvrf while the source and destination addresses of the inside packet belong to the ivrf.
Front door vrfs seem to cause a lot of confusion.
This type of vrf is called a fvrf or front end vrf.
Vrf aware ipsec vrf aware ipsec に関する制約事項2 vrf aware ipsec に関する制約事項 暗号マップ設定を使用して vrf aware ipsec 機能を設定し inside vrf ivrf が front door vrf fvrf とは異なる場合 unicast reverse path forwarding urpf.
In this blog fish goes delves into the whys the hows and the how it works in a simple easy way.
By using front door vrf we are isolating transport network usually internet facing and this allows us to configure default route that won t interfere with routing in our global table.
If no vrf aware config is used everything is done in the global vrf and all interfaces are in the global vrf.
Front door vrf or outside vrf the vrf that contain the encrypted traffic global vrf.
The outer encapsulated packet belongs to one vrf domain which we shall call the fvrf while the inner protected ip packet belongs to another domain called the ivrf.